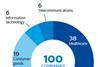
While companies generally perceived cyber security as a key organisational risk, very few communicated that they have policies, governance structures and processes that were effective at tackling cyber threats.
For example:
- a fifth of companies provided information against two or less of the 14 indicators assessed;
- over 30% did not explicitly indicate that they comply with data protection and cyber security laws;
- nearly 60% did not indicate that their board or board sub-committee was responsible for cyber security-related issues;
- less than two-thirds provided little or no information about the frequency and channels of communication to the board;
- less than half (31%) had access to internal or external expertise through industry collaboration or via access to external consultants; and
- only 15% of companies indicated that they provided cyber security training to all staff, and only 17% indicated that they conduct regular audits.
Disclosure levels were weakest in the healthcare sector, potentially pointing to a less advanced cyber security posture. This is particularly problematic as this sector is responsible for storing and handling highly personal and sensitive data. Stolen healthcare credentials are claimed to be 10-20 times more valuable than the credit card details of targeted individuals as they allow hackers to create fake IDs for buying medications and medical equipment, or to make false insurance claims.
In contrast, telecommunication and financial services companies provided the most robust disclosure on cyber security issues, disclosing against seven indicators on average. Given both types of companies provide critical network infrastructure (CNI), they generally have sophisticated cyber defences.
US companies, on average, scored better in disclosing cyber security practices than companies in other regions, despite operating in a jurisdiction with comparatively underdeveloped cyber security legislation. Much of the US cyber security regulatory environment is decentralised and determined at the state level. The EU, on the other hand, has stricter data protection controls and regulatory standards, most recently through the General Data Protection Regulation (GDPR).
This report goes into greater detail about observed trends and gaps in disclosure, and suggests topics investors can cover in their dialogue with companies on cyber security. The engagement dialogue may also enable investors to formalise a view on minimum disclosure expectations.
Examples of cyber security breaches
Retail: Home Depot
When: April-September 2014
Impact: theft of email addresses and card payment data affecting over 50 million users.
Summary: in September 2014, the company announced that its payment systems, provided by a third party, had been infected with malware. This affected people who used payment cards on its self-checkout terminals in US and Canadian stores between April and September 2014, compromising their payment card information. The company made significant compensation payments (US$19.5 million to US customers and US$25 million to affected financial institutions).
Financial: Equifax
When: May-July 2017
Impact: theft of personal information, as well as the credit card numbers of 209,000 customers, affecting 145 million US customers in total. Further investigation revealed that the details of another 2.4 million US customers were stolen. The estimated cost of the breach is now more than $439 million.
Summary: the breach was due to a flaw in a tool used to create web applications, which hackers exploited to take control of the Equifax website.
Stepping up governance on cyber security
- 1
- 2Currently reading
Research takeaways
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14