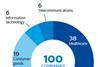
12. Does the company conduct audits of information/cyber security policies and systems?
Only 17% of companies indicated that they conduct regular audits.
Investor relevance: independent audits test the robustness of cyber security measures within a company, flag vulnerabilities in the company’s security posture and result in action plans to better implement the organisational cyber security strategy. Investors could discuss with companies whether they undertake independent audits and, if so, how frequenty. Questions may also be raised about industry practices, best practice approaches and regulatory requirements around assurance, and how this aligns with a company’s strategy.
Good practice: guidance such as the NIST and CBEST frameworks have been used to drive good practice at organisations. The CBEST framework, produced by the Bank of England, recommends regular penetration testing whereby a cyber attack is simulated using an accredited penetration testing service provider to test the firm’s cyber security defences. The process is intelligence-led and based on information on the greatest threat and how a firm could be attacked. The US NIST framework, a voluntary set of guidelines, standards and best practices to manage cyber security-related risks, also provides comprehensive information on controls and certifications.
Inditex provides comprehensive disclosure against this indicator, outlining both internal and external auditing mechanisms and the reasons for them: “The IT security area within the IT division relies on continuous review mechanisms, which are regularly assessed by different internal and external audits, to prevent, detect and respond to any potential cyber attack. Such controls would allow advancing and/or reducing the consequences of risk materialisation, together with insurance policies covering loss of profit, expenses stemming from cyber attack and public liability of the company for damages incurred by third parties […] The company considers, based upon the available information, that these controls have been successful to date.”
Stepping up governance on cyber security
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10Currently reading
Indicator 12: assessment
- 11
- 12
- 13
- 14